

Spoofing, or DNS cache poisoning, is a type of attack that is focused on corrupting the cached answers on DNS servers with recursion enabled, either through software exploits or protocol weakness. Software exploits can be patched with software updates, but protocol weakness can only be updated with protocol fixes or extensions. DNSSEC is the “fix” for the traditional DNS protocol.
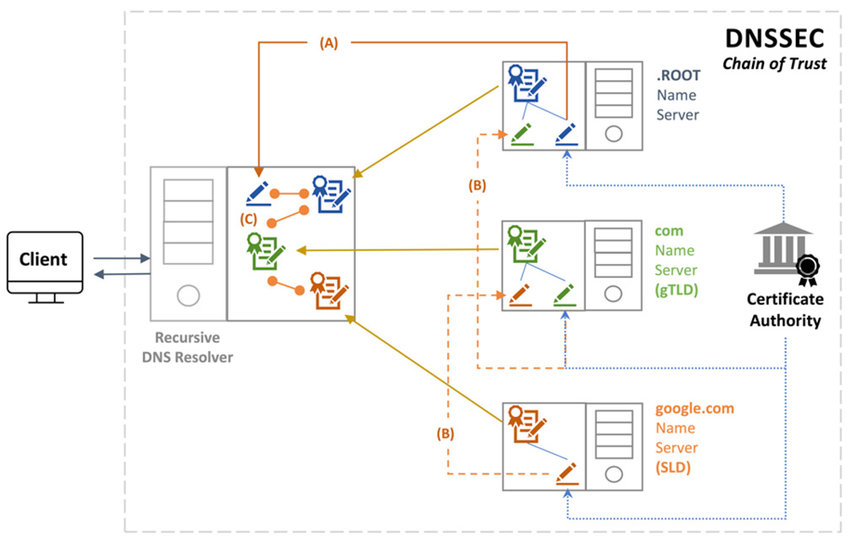
DNSSEC aims to provide a globally distributed database that can be fully validated. It accomplishes this by using public key cryptography to authenticate each message, ensuring it originated from the right source, and the content remains unaltered. All of the cryptographic information is stored in DNS itself, published as additional DNS records. A DNSSEC-enabled resolver (knowns as validating resolver) can chase up the DNS hierarchy, from example.com to .com to root, validating every layer.
A form of man-in-the-middle attack where attackers flood a DNS resolver with false DNS information. Sometimes these attacks can get a match by the law of large numbers and plant a false result into the cache of the DNS resolver. The DNS resolver then provides this erroneous or malicious web address to anyone seeking that website until the time-to-live (TTL) expires.
DNSSEC also protects against malicious DNS attacks that exploit the DNS system and provide phony results for zones that don't even exist, essentially exploiting gaps between zones. DNSSEC secures the entire zone and provides mechanisms to prevent gap exploitation in unsigned zones. This is also known as the authenticated denial of existence.
The need to design a backward compatible standard that can scale to the size of the Internet is extremely difficult
​​​​​​​An important part of DNSSEC is the ability to authoritatively assert that a given name does not exist.
​​​​​​​Deploying DNSSEC across a wide variety of DNS servers and resolvers takes time.
​​​​​​​There have been disagreements of over who should own the top-level domain root keys.
It has been hard to overcome the perceived complexity of DNSSEC and DNSSEC deployment.